Antivirus Flags Trojan Malware In WordPress 6.6.1 Version
Last week, WordPress released a new version 6.6.1 to address fatal errors in the WordPress 6.6 version.
But now another piece of news is getting viral all over the Internet related to trojan malware in the WordPress 6.6.1 version.
Multiple users have reported trojan alerts and web host lockdowns.
Antivirus Flags Trojan in the Latest WordPress Version
A user detected a virus issue, i.e. WordPress-6.6.1.zip showed a virus from Windows Defender and reported it immediately at the official WordPress.org help forum.
The user even attached a screenshot highlighting the trojan alert which clearly stated that the WordPress zip file version 6.6.1 “is dangerous and executes commands from an attacker” and that the quarantine process had failed.
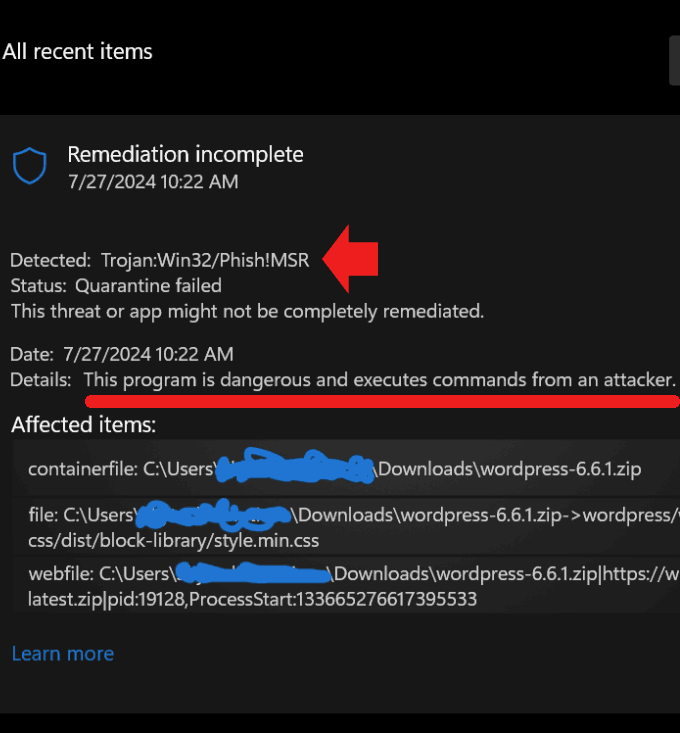
Soon similar concerns from other users were noticed and highlighted in the forum.
Another user stated that a specific string in the CSS file is being detected as a Trojan virus.
Is There Anything To Worry?
A false positive is typically a result that shows up as positive even when it doesn’t correspond with the result of the test. WordPress users rapidly realized that the alert for the Windows Defender trojan infection was a false positive.
As per the official WordPress GitHub ticket filed, the root cause of the problem was found to be an insecure URL (http versus https) that is referenced from within the CSS style sheet. Since a URL isn’t usually regarded as a component of a CSS file, Windows Defender may have identified this particular CSS file as hiding a trojan.
This is the point at which events took an unforeseen turn. It should have been the end of the story, but someone started another WordPress GitHub issue to record a suggested patch for the insecure URL, which ultimately led to the revelation of what was actually happening.
http://www.w3.org/2000/svg is the insecure URL that required a fix.
The individual who opened the ticket changed the file with a version that included a link to the HTTPS version and soon things were back to normal.
Remember, the “insecure” URL is actually an identifier that defines the scope of the Scalable Vector Graphics (SVG) language within XML, not a connection to a file source (and hence not insecure).
Basically, nothing was wrong with WordPress 6.6.1 but a minor issue in Windows Defender that failed to identify an “XML namespace properly”.
If you also got goosebumps reading the headline, it is fine.
Your WordPress Latest Version is good to go.
